06 Apr 22
Today is day 96 of year three of flatten the curve for two weeks. So, let’s talk more about what enterprise fraud actually is, how to identify it and why it’s a perfect and fulsome explanation for what people mistakenly call the “COVID-19 pandemic.” That’s how we’ll get this one going and if you’re new to Moonshine, this is where we hang our hat – evidencing COVID-19 as a construct of enterprise fraud. If you’re already swilling the ‘Shine, you’ll know that I’m taking you down an avenue that will stack-up further evidence behind the existing 300 or so articles already stacked-up.
[“Van life”, required travel and other obligations has this article slated for 30 Mar 22 being late in its publication.]
Here is a visual depiction of the cyclical, seasonal and annual nature of the COVID-19 enterprise fraud construct:
Relative to that construct, a criminal enterprise exists under RICO statute, which is the federal law under which COVID-19 crimes are prosecutable. In short, most folks likely define RICO statute by its common vernacular term “organized crime.” The criminal enterprise is the collective group of offenders committing the coordinated crimes in methodical fashion.
From the U.S. Office of Justice Programs,
RICO is Title IX of the Organized Crime Control Act of 1970, although it has broad application beyond the context of organized crime, because Congress mandated that RICO “be liberally construed to effectuate its remedial purposes.” The U.S. Supreme Court has held that RICO may be applied to legitimate businesses and to enterprises without a profit motive. To prosecute a defendant under RICO, the government must prove that the defendant, through the commission of two or more acts that constitute a pattern of racketeering activity, directly or indirectly invested in, maintained an interest in, or participated in an enterprise, the activities of which affected interstate or foreign commerce. Courts have found that public entities and governmental agencies, as well as private entities, can constitute RICO enterprises. Also, a combination of different entities can constitute an enterprise within the meaning of RICO. In discussing defenses to RICO, the article assesses the results when one or more underlying predicate acts that supports a RICO offense is invalidated, the statute of limitations for criminal and civil RICO violations, a defendant’s withdrawal from a conspiracy as a defense, preemption challenges to RICO, challenges based on the “primary jurisdiction” or “horizontal preemption” defense, and defense approaches that use a “reverse vertical preemption” theory. Constitutional challenges to RICO are also considered. Following a review of the criminal and civil penalties under RICO, an overview of recent developments in the RICO statute focuses on protests, tobacco litigation, health care fraud, divorce, and police misconduct.
U.S. Office of Justice Programs
According to U.S. RICO statute and the legal definitions therein an,
“enterprise” includes any individual, partnership, corporation, association, or other legal entity, and any union or group of individuals associated in fact although not a legal entity.
Cornell Law Quoting RICO Statute
In an article I wrote last November, I discussed the COVID-19 criminal enterprise in incomplete fashion,
The primary components and entities also contain the individuals comprising the Criminal Enterprise under RICO. This enterprise has engaged in evidenced RICO patterns and has severe legal exposure under RICO. They are identified as but not necessarily limited to the WHO, UN, CDC, HHS, FDA, NIH, NIAID, NVSS, CDM, DHS, FEMA, DOD, DOJ, ASPR, Johns Hopkins and the Bill and Melinda Gates Foundation. As Martin puts it, “You can’t find a person promoting this scenario [pandemic] that’s not part of the interlocking directorates of the WHO, the CDC, the NIAID or the organizations that are the philanthropic cover organizations that fund them.”
Political Moonshine
Here are a few of the individuals in this criminal enterprise:
To really understand the depth and breadth of the COVID enterprise fraud construct, come to comprehend the malignant tendrils that extend from it to permeate about every granular aspect of our lives. Develop comprehension for how how all of the individuals and entities in the schematic below fit together so precisely. That work is already done and sitting in the Moonshine archives.
To put the cart in front of the horse and getting to the back-end of conspirators, conspiracy, enterprise fraud and treason, the collective of criminals would certainly never engage in crimes against humanity with such enormous consequences for getting caught if no direct benefit were to be had. It’s basic math: 1-engage in crimes and treason to manufacture the foundation for future criminality, 2-upon the foundation being laid, unroll the multi-purpose COVID construct to steal the election and insert the proxy – Joe Biden – who is running point for Barack Obama’s third term and 3-receive financial and other dividends for service to the construct and the Globalist power brokers in the backdrop.
Case in point:
Question: In a scenario where the criminal enterprise leverages a viral pandemic as the context of for its enterprise fraud construct, what types of actions would the criminal enterprise be obligated to take?
Answer: 1-Change existing rules, regulations, laws, etc., 2-Construct false scenarios and data points to permit exercising “emergency authority,” 3-Exploit “emergency authority” to circumvent regular constitutional governance and impose unlawful mandates, 4-Harvest and construct fraudulent data for propagation, 5-Create a narrative supported by constructed data, 6-Revise, manage and control data and narratives, 7-Organize and communicate the narrative and data, 8-Organize and communicate narrative and data publication strategies, 9-Revise narrative as needed, 10-Manipulate or delete inconvenient data contradictory to the established narrative, and 11-Withhold effective treatments to ensure perpetuity and maximize damage. That’s a short and basic list that ought to sound familiar.
Let’s talk apples and specifically, apples-to-apples. By that, I mean having one apple [flu/pneumonia season] to propagate as another apple [SARS-CoV-2.] We brand it apples-to-apples because I can’t sell an orange as an apple for obvious reasons. It’s the same here. Flu/pneumo can’t be sold as SARS-CoV-2 if they aren’t an apples-to-apples match. It looks like this:
The COVID criminal enterprise needed to bioengineer an apples-to-apples pathogen that can be propagated with data harvested from a readily available and reliable data reservoir. In the case of COVID-19, a primary data reservoir is flu/pneumonia season.
SARS-CoV-2 is the perfect design to permit propagating flu/pneumo infection and mortality data as “COVID” data because there’s little difference between the symptoms of SARS-CoV-2 and flu/pneumo. I have evidenced this extensively in a stack of articles and the Moonshine COVID timeline is a good place to start-in on them.
Apples-to-apples permits the harvesting of data from associated comorbidities as diagrammed below:
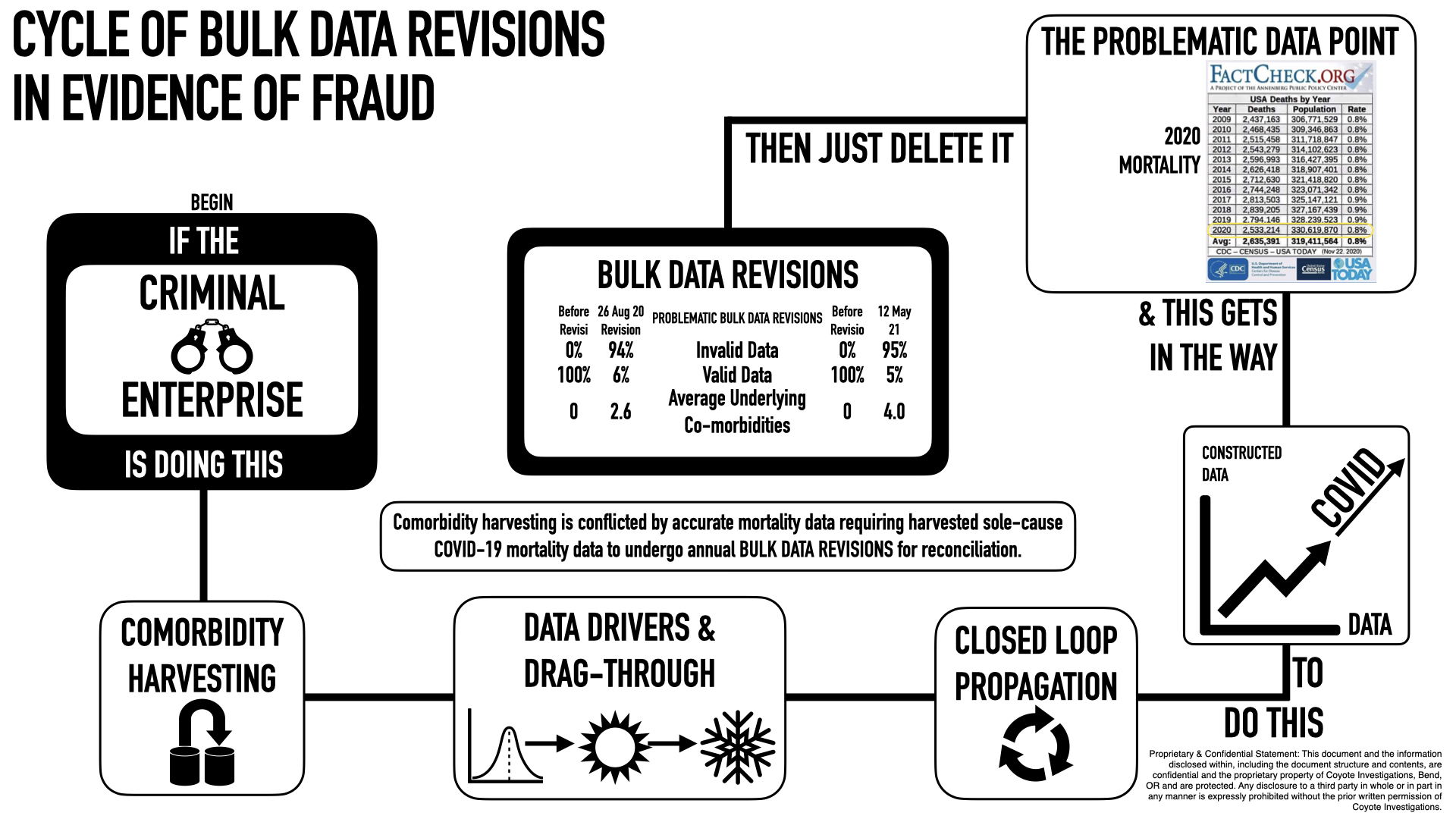
The problem with harvesting comorbidity data to propagate as COVID-19 data is that it causes problematic data points requiring back-end data revisions, which often times take the form of deleting bulk data sets altogether.
The greatest problematic data point to COVID is actual mortality data; especially that from 2020, which has been scrubbed from the internet. This is old work below with a projection of 2020 mortality data presented alongside the actual and statistically worse 2020 mortality data.
For the sake of brevity our focus here will be data deletions evidenced by a change of rules. They presented very early in the construct for anyone not drinking the MSM Kool-Aid and willing to parse-out some basic numbers antithetical to the ones being propagandized. This early evidence depicts a pattern that is still ongoing today:
This pattern of data manipulation was permitted by a significant rules change. In mid-April 2020 and just moths after the “outbreak” occurred, the criminal enterprise changed the rules by moving away from the gold standard, benchmark pandemic measurement of mortality data, which was in decline at the time.
This permitted the criminal enterprise to focus on infection data and a newly minted but made-up term “new cases.” This is what enterprise fraud looks like: changing longstanding and gold standard rules to introduce new fictitious terms that predicate emergency use authorizations that circumvent regular constitutional governance that directly benefits the criminal enterprise relative to its tactical and other objectives.
Here’s what it looks like in real life when when comorbidity data is harvested and propagated as a [Delta] variant of SARS-CoV-2:
I continue to state that “these people play inside of a box.” The “box” is the fraud construct the criminal enterprise engineered because it’s entirely built around existing rules, regulations, laws, organizations, departments agencies, authority, etc. It presents with firm boundaries and altogether, the “box” allows or disallows things to occur inside of it. Once you understand the “box” you can make accurate predictions about the criminal enterprise and I’ve made and evidenced them by the boatload relative to COVID; not being shy about stating such, either. Here’s the most recent one also posted on Telegram:
Ultimately and due to the cyclical, seasonal and annual nature of the construct – the “box” – the data deletions that must be conducted to continue driving the construct’s fraudulent narrative become cyclical, seasonal and annual, too; and if they aren’t made, the narrative collapses in on itself. It manifests as an exercise in pattern recognition, which is a Moonshine specialty. Here is direct evidence of this:
As another example of back-end revisions to data and data sets, I copiously evidenced the 5-8 week rolling window in the death certificate process in the article It Starts With A Code [and in Part II, which maps-out all of the fraudulent skews in the ICDM-10 Coding Manual.] This permits the criminal enterprise to state one cause of death and then revise it later when no one is watching or alert to it. Think of it as “died of this” then but “really died of that” later, when no one is watching. These images are from the article and detail it:
We even extrapolated the 5-8 week death certificate revision window all of the way down to the state level and in this case, in my pre-van life state of Oregon and as per corrupt and complicit governor Kate Brown. She’s owned by China.
That’s direct evidence of a constructed enterprise fraud mechanism deriving from China vis-a-vis the United Nations/WHO and right down to a U.S. state level.
Another example of inconvenient data requiring bulk data set revision and deletion unnervingly occurred more recently in the form of the CDC’s deletion of pediatric mortality data. I covered it in a recent article. This extract comes from the article.
This brings us to the most recent example of the COVID-19 criminal enterprise managing data and narratives that take the form of inconvenient bulk data set deletions. We’ll rely on a full and brief write-up by Just the News entitled ‘NIH deleted COVID info from public view at Wuhan researcher’s request, emails show’ to lay it out for us. From it,
The National Institutes of Health deleted information from public view about COVID-19 genetic sequencing during the pandemic at the request of researchers in Wuhan, China, a move that created consternation in science circles, according to emails obtained by a nonpartisan whistleblower and government oversight group.
The emails obtained by the Empower Oversight group show a Wuhan University researcher submitted virus sequence information to the NIH’s Sequence Read Archive in March 2020 – the same month the World Health Organization declared a pandemic and about two months after the virus was detected in Wuhan.
The scientist made an additional submission on the virus in June 2020, according to the emails. Later that day, he asked the NIH to retract the submission, claiming it was made in error.
The NIH responded by saying it preferred to edit or replace submissions over replacing them.
A few days later, the researcher submitted another request to withdraw the genetic sequence from the NIH database, according to the emails.
The NIH agreed to the researcher’s request one day later, and asked for clarification on whether another submission should be deleted.
“I had withdrawn everything,” an unnamed NIH official said to the Wuhan researcher in an email.
NIH acknowledges the data was withdrawn from public view but says it has archival copies.
The emails were obtained after Empower Oversight sued the NIH under the Freedom of Information Act. You can read them here.
The documents also show an expert advised then-NIH Director Francis Collins and Dr. Anthony Fauci, who leads the agency’s National Institute of Allergy and Infectious Diseases, that COVID originated outside of the Wuhan food market, as the Chinese government has claimed.
Additional emails show that the NIH directed reporters to more favorable coverage about the deletion.
“Off the record: we think this WaPo story does a good job characterizing the situation,” NIH’s Renate Myles wrote to a reporter at The Hill newspaper, directing the journalist away from a New York Times story because of its “tone.”
“These documents raise several questions that need further investigation to answer fully,” according to a report by Empower Oversight, founder by a former top staffer for Iowa GOP Sen. Chuck Grassley. “Congress should press the NIH for answers on why it is stonewalling Senate inquiries and dragging its feet on basic transparency through FOIA.”
The group says one of the most disconcerting elements of the emails is evidence showing the NIH has refused to participate in a transparent process to examine data on the deleted sequences.
“Most importantly, why has NIH refused to examine archival copies of deleted sequences in an open scientific process to determine whether any of that information might be able to shed light on the origins of the COVID-19 pandemic?” the group asked.
However, that argument was dismissed by NIH official Steve Sherry.
Although sequences are never fully deleted, according to the agency, Sherry told a researcher who asked for transparency, “As you know, when data sets are withdrawn from the database, that status does not permit use for further analyses.”
Madeleine Hubbard – Just the News
Here is a link to the full 238-page document accompanying the article, which I’ve reviewed in full. It’s entirely revealing relative to bulk data set revisions and the broader enterprise fraud I’ve outlined as supported by the vast and deep evidence of it:
nih-foia-request-56712_redacted*The PDF is too large for the preview function so it can be viewed from the included link or downloaded and viewed per the PDF download link.
From the document we get the following documentation, which further contributes to and evidences a construct of enterprise fraud being executed by a criminal enterprise as defined by RICO statute. As you read them, pay attention to the redaction codes and specifically (b) (5) and (b) (6). Here’s why [emphasis mine]: (b) (5) is the redaction code for “Reveal formally named or numbered U.S. military war plans that remain in effect, or reveal operational or tactical elements of prior plans that are contained in such active plans” and (b) (6) is the redaction code for “Reveal information, including foreign government information, that would cause serious harm to relations between the United States and a foreign government, or to ongoing diplomatic activities of the United States.”
Do you find it peculiar that email and other documentation deriving from a so called and supposedly authentic “pandemic” requires redactions for military war plans? For considerations of serious harm to foreign diplomacy? It’s because the “pandemic” is a construct of enterprise fraud serving as a mechanism to overthrow the U.S., which is an act of war. Period. The Moonshine archives has been directly and copiously explaining this all since Spring 2020 and even before; and it’s all backed by evidence stacked to the moon.
I’d encourage folks to take a spin through the entire 238-page document to examine the relevant pages. Here’s a shot glass full to give you an idea.
The U.S. has been defrauded by a mechanism for overthrow and is on its way to the CCP’s brand of communism. It will put all of humanity on a technocratic global plantation and the fall of the U.S. is required to make that happen. It’s why we’re being ushered into a multiple front war with Russia over Ukraine and China over Taiwan/South China Sea and further, it’s why I predicted that exact scenario right down to the very timeline and long before Putin made any incursion into China. [Here’s the latest article on that topic with links to the 25 that precede it.]
It’s also why our team has filed a federal grand jury petition in the Ninth Circuit naming the current and former directors of the CDC as defendants. It’s also why our team will continue its efforts.
The more that Americans are armed with the truth, the more likely we’ll have success with our efforts. Hope and pray we are successful. Please spread the Moonshine far and wide – that’s a direct request for posterity’s sake.
-End-
Leave a Reply to RUSSIA, UKRAINE, CHINA and COVID-19: Predicted New Variants Arrive Right On Time, Milley Warns of “Significant International Conflict Between Great Powers” – POLITICAL MOONSHINECancel reply